2 minutes
Security Flaw in the KNUST AIM Application
The Academic Information Manager (AIM) is the official mobile application for KNUST students. The key functions of AIM include: course registration, checking of results, editing of personal records, access to news from the University’s website, notifications and checking of fees. This research presents a flaw in the bearer authorization token implementation in the REST API for the AIM app. This authorization token is not validated per user basis, hence can be exploited to access or modify any student’s information through the REST API.

Security Flaw
This section explains the details of the security flaw.
Application Version
Operating System: Android
Version: 1.0.13.2
Release Date: 18th September, 2018
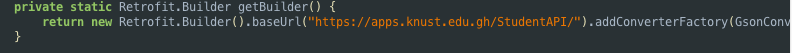
The REST API base url for the AIM application is
https://apps.knust.edu.gh/StudentAPI/
This is shown below.
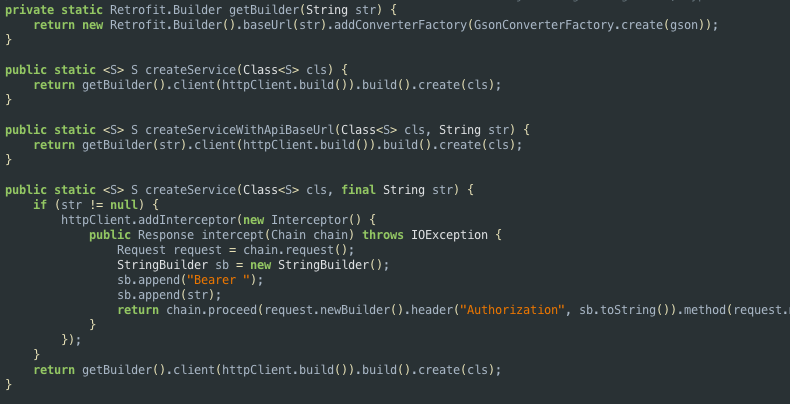
The AIM REST API uses bearer token to allow access to the associated resources [1]. The implementation of the bearer token verification in the mobile application is shown below.
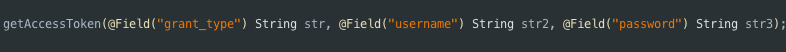
The bearer token is generated when a user logs in with his reference number and password. The parameters for the REST API is shown below.
A sample C# implementation of the authentication request and the token generated are shown below.
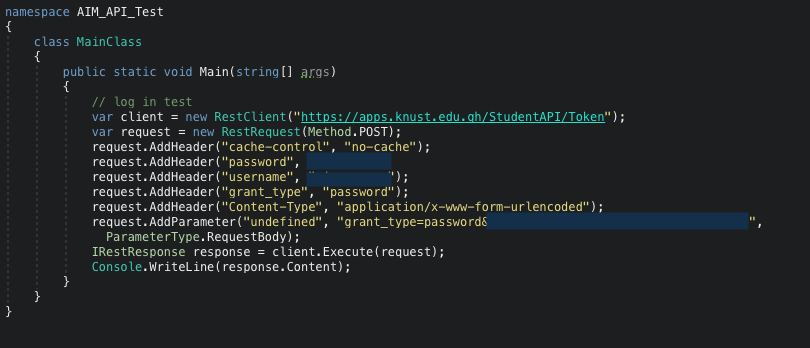
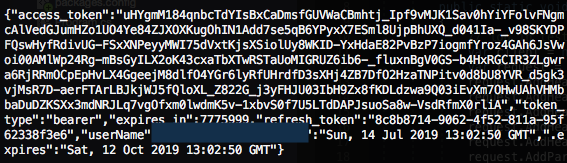
The bearer token is a very good security implementation. The problem lies in the fact that a valid bearer token of a particular student can be used to access or modify other students’ information once the reference number is known.
References
- RFC670, “The OAuth 2.0 Authorization Framework: Bearer Token Usage”, Internet Engineering Task Force (IETF), 2012.